-
Posts
323 -
Joined
-
Last visited
-
Days Won
5
Everything posted by jodunno
-
I just want to add a different opinion to the subject. I am more into speed and efficiency and i am always willing to rewrite my own code to find faster and better ways of accomplishing the same tasks. I've spent three years rewriting my website code and it is faster, smarter and better than all of the previous code. I do hate the fact that we do not yet have vision code or machine learning code in php (built-in features added to the language). Vision would be nice here but coding it will be a pain. Anyway, i hate it when people make unnecessary variables and also use long variable names. Each letter used in a variable name is stored in memory. Memory saving code is always better, no matter what someone else will say. I have started using single letter variables and i love it. The code is cleaner and easier to read. Sometimes a legend is necessary as a multi-line comment but the single character variable works. OP: The names array should not be coded in such a manner if it is not to be used in the manner that it is coded (bob_smith will be used as bob_smith). I think that once you start finding reasons to separate the names (last name only), you will discover that this method is not a good idea. I do not know why php coders waste memory with variables and variable names but complain about multi-dimensional arrays. I would rather see someone use a database or a multi-dimensional array when it comes to names. Gizmola pointed out rank, such as Senior (Sr.) or Junior (Jr.), which is a good point. Other naming conventions will also cause a problem. I think that anyone in this position should use a multi-dimensional array which separates first and last names, stores titles and ranks et cetera. Then finding matching names is easier and it simplifies performing other data crunching ideas that have yet to be thought of. And it becomes easier to add info to the arrays or remove info from the arrays. as a note for users that want to save memory, i am including example code that reuses the foreach variable, rather than creating a second or third variable. Also, this code is 2-3 milliseconds faster. I am certain that this code can also be tweaked for speed and memory but it serves as a model of code reusability and memory-saving techniques. I'd like to see more people writing faster, smarter, better code - myself included. $names = ['bob_jones', 'sam_smith', 'jane_doe', 'john_smith', 'jill_jackson', 'matt_jones', 'john_doe', 'emily_smith']; $sn = []; //surnames foreach ($names as $x) { $x = substr($x, strpos($x, '_') +1); empty($sn[$x]) ? $sn[$x] = 1 : $sn[$x]++; } print_r($sn);
-

php segmentation fault when connecting to Access database
jodunno replied to raphael75's topic in PHP Coding Help
I'm just wondering if you have both odbc extensions installed? since you only show the pdo_odbc extension. I thought that both extensions are required. I do not use Linux or ODBC but i have both extensions installed in FreeBSD. $ pkg search -x ^.*\-odbc.*\- php83-odbc-8.3.19_1 php84-odbc-8.4.5_1 $ pkg search -x ^.*\-pdo_odbc.*\- php83-pdo_odbc-8.3.19_1 php84-pdo_odbc-8.4.5_1 /usr/local/etc/php/ext-20-odbc.ini /usr/local/etc/php/ext-30-pdo_odbc.ini certainly there could be an issue with the extension but it will be nice to know if you have both extensions installed and enabled. -
Hi CBG, @mac_gyver actually posted the solution that you have chosen. And i want to say that mac_gyver and maxxd are better programmers and they have more experience than i do in this field. However, i disagree with any solutions that create a bunch of if branches because every step that a program takes can really slow it down. I definitely disagree that you cannot check it all at once. Personally, i recommend using the tools in the PHP toolbox to your advantage. I would do the following and be done with it: <?php $p = 'Yes'; $d = 'No'; $c = 'No'; $o = 'No'; $pinary = [$p] === ['Yes']; $nerror = [$d, $c, $o] === ['No','No','No']; if ($p && $nerror) { echo 'error'; exit; } echo 'No errors detected'; ?> then i would unset $pinary and $nerror to spare memory (even though 100% of coders would tell you not to do that). My point, is that you can check it all at once but you could do it differently. I would define an error and simply check if it is true.
-
Hi CBG, Logical switches do not work like spoken words and it is easy to misunderstand them. What you really want to check is that if any one of d,c,o is yes, then error. But PHP is obeying your instructions by stopping when anyone of them is No. You need to switch the OR to an AND and it will catch the one Yes that is not allowed: <?php $p = "Yes"; //yes is different than Yes $d = "No"; $c = "No"; $o = "No"; if ($p === "Yes" && $d !== "Yes" && $c !== "Yes" && $o !== "Yes") { echo "error"; exit; } echo 'no errors'; ?> which will display an error if all three (d,c,o) are No. Otherwise, the code will display no errors. but what are you doing when a lowercase y is used? yes instead of Yes. maybe you should also use lowercase and compare with strtolower().
-
Hi Rhaoma, umm, I didn't imply or intend to imply that you write "sh1t code". I am not exactly a top notch coder. I actually write some ugly Spaghetti code at times. Noone would say that my coding skills are that to be admired, so i definitely do not insult other coders. Not sh1t code. I just see a 100 and i wonder what you are doing but i do not know how i solved any problems for you. If your code is working and you are happy with the code, then i suppose that you have solved your own problem. Otherwise, let us know if you are still having trouble. The forum has alot of pro php coders. Sometimes people get busy and may not respond immediately but someone will eventually come along and help. I hope that you have a pleasant day, John
-
where in the hell-p do you get 100 for the Content-Length? what is that supposed to mean? 100 what? sheep? usually, programmers let php determine the size of something. filesize, strlen() etc. I think that you should take a closer look at your code.
-

Removing / editing certain keywords from array content
jodunno replied to shamuraq's topic in Regex Help
Python? in a php forum? forums.phpfreaks.com. I do not see the name python in the domain. I hate python and it is not necessary. PHP can solve this problem and any other problem. Please see the solution posted by Barand: Furthermore, isolating the actual question is not a problem if the array is designed/structured correctly from the start. So a better reply would be a suggestion other than that already posted by Barand. one could simply rewrite the array using a loop, then regex is not even necessary. In other words, fix the array to hold three components instead of a single string (a problem created by bad array design/structure). So, to me, the problem is the array. one could use php to rebuild the array or just use the following code to get what you want from the array (however Barand has already posted a solution that works): <?php //add a loop to build a new array or just display the question of the current array (but in latter case, the solution by Barrand is better) //to repeat Requinix: be sure that the questions actually contain the filtered characters or you will further complicate the matter. $qlist = array (); $qlist[0] = "[Question - Geography Chapter2] How would you describe humans' relationship with the physical environment? (Page 42)"; list($source, $question) = explode("]",$qlist[0]); //echo "<p>$question</p>"; list($question, $page) = explode("(",$question); echo "<p>$question</p>"; ?> -
regarding background-size: i wonder if actually specifying a size is not working? if i understand you correctly, you want to force a background image to fit into its container, yes? I made a crop of a photo of mine depicting the female genitalia of Phaonia rufipalpis. I will attach the crop for testing my code. I use background-size to make it fit the container. Is this not what you want? <!DOCTYPE html> <html> <head> <title>CSS background-size</title> <style> div.container { display: block; margin: 0 auto; padding: 0px; width: 400px; height: 400px; border: solid 1px #000000; background-image: url('s263x200.jpg'); background-repeat: no-repeat; /* background-size: 400px 400px; */ background-size: 100% 100%; } div.text { position: relative; top: 93%; padding: 5px; background: rgb(0,0,0,0.2); color: #ffffff; text-align: center; } </style> </head> <body> <div class="container"> <div class="text">background-size: 100% 100%;</div> </div> </body> </html>
-
that is where the expression Spaghetti code comes into play (weaving in-and-out of a language creates a noodle like appearance) and fortifies why it should be avoided if posible. Once you exit php, how is php to know that the else belongs to the previous if without further clarification? when php encounters the else, it responds with the error because an if does not precede it in the same section of code. Adding curly braces removes the ambiguity, or using end if as suggested by Gizmola.
-
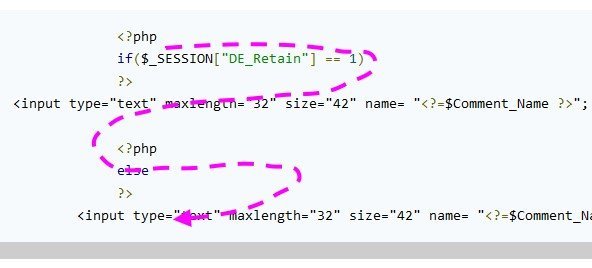
Hi Paul-D, you are moving in-and-out of php (spaghetti code). You will need to use the curly braces in your branch, so that php knows that the else belongs to the previous if statement. You can echo or print by using a single-quote, double-quote combo: echo 'i can use "double-quotes" within single quotes'; <?php session_start(); $_SESSION["DE_Retain"] = 0; if(!empty($_SESSION["DE_Retain"])) { echo 'show if'; } else { echo 'show else'; } $x = 1; if ($x == 1) { ?> x = 0 <?php } else { ?> x = 0 <?php } ?> you should avoid spaghetti code whenever possible. Sometimes it is okay but an entire php script written with spaghetti code is very difficult to follow and you will find yourself asking alot of questions in phpfreaks forum because it is difficult to debug such code. edit: I meant to type x = 1. sorry.
-
my usage of htmlspecialchars is to protect you from someone trying, for example, JavaScript code in place of a name. Atleast htmlspecialchars would prevent the execution of code. You shouldn't use it on a username, email address, password etc. You will instead need to employ some sort of validation, such as regex to check names and numbers. ENT_QUOTES just converts quotations ("). session_destroy: i do not know what you are creating/developing but a login/logout process will be a good idea. However, the session will be lost whenever the user closes the browser unless you are maintaining state with cookies. You could add a logout or destroy session button, which is a post to the test-sesh2.php page. Then in test-sesh2.php, detect a post with your destroy session input and implemement a session_destroy command: if isset $POST 'destroy' then session_destroy(); let us know if you need help implementing session_destroy or validating input...
-
but it looks and functions like a login. You even refer to the poster as User in test-sesh2.php I feel compelled to mention that it is, in fact, a login of sorts. Anyway, i'm sure that this post will attract alot of helpful posts because your code is insecure among other things. I will just point out what makes it function and leave the rest to other members. here you are assigning the post values to php variables ($name and $number) instead of session variables AND you are checking if 'submit' is set but your input type submit name is actually 'register'. If you cannot remember 'register', then change it to 'submit' to avoid further complication. Thus, if you correct these errors, then your session test should work. But you shouldn't be assigning input to variables of any type without validating and filtering. Furthermore, if a User should be remembered longterm, then switch to a database for storing names and numbers and leave the session out of it. test-sesh.php <?php session_start(); if ($_SERVER['REQUEST_METHOD'] === 'POST') { if (isset($_POST['register'])) { if (!empty($_POST['name']) && !empty($_POST['number'])) { $_SESSION['name'] = htmlspecialchars($_POST['name'], ENT_QUOTES); $_SESSION['number'] = htmlspecialchars($_POST['number'], ENT_QUOTES); } } } if (isset($_SESSION['name'])) { header("Location: test-sesh-2.php"); exit; } ?> <!DOCTYPE html> <html> <head> <title>Test $_SESSION</title> </head> <body> <h1>Test $_SESSION</h1> <form method="post"> <label for="name">Name:</label> <input type="text" name="name" required><br> <label for="number">Number:</label> <input type="text" name="number" required><br> <button type="submit" name="register">Submit</button> </form> </body> </html> test-sesh2.php <?php session_start(); if (!isset($_SESSION['number'])) { header("Location: test-sesh.php"); exit; } ?> <!DOCTYPE html> <html> <head> <title>User Dashboard</title> </head> <body> <h1><?php echo $_SESSION['name']." ".$_SESSION['number']; ?></h1> </body> </html> I hope that this helps, John
-
You have not reponded, so i want to add a second (uri method, in case you are actually trying to load a second page). My example requires an index.html page, a directory named target which contains its own index.html page. index.html at the root: <!DOCTYPE html> <html> <head> <title>CSS :target Practice</title> </head> <body> <h1>CSS :target Practice</h1> <p><a href="target/index.html#tab1">Short Description 1</a></p> <p><a href="target/index.html#tab2">Short Description 2</a></p> </body> </html> index.html in the target directory: <!DOCTYPE html> <html> <head> <title>CSS :target Practice</title> <style> ul.tabs { margin: 0px; padding: 4px; list-style-type: none; font-weight: bold; } .li { padding: 4px; border: solid 1px #ffffff; background: #ffffff; } #tab2content { display: none; } :target { border: solid 1px #009900; background: #e0e0e0; } #tab2:target { font-size: 24pt; } #tab2:target > #tab2content { display: block; } </style> </head> <body> <h1>CSS :target Practice</h1> <p>The target will be active per css (working in modern browsers: Edge/Chrome, Firefox, Opera and Safari)</p> <ul class="tabs"> <li id="tab1">!Product Enquiry</li> <li id="tab2">Product Enquiry <ul id="tab2content"><li>Hello Product seeker</li></ul></li> </ul> </body> </html> Perhaps you can let us know if you figured it out or not, John
-
target has plenty of documentation, so you shouldn't have a problem implementing it into your code. I do not use wordpress stuff and i cannot help you with that code but here is a sample of target practice and you should be able to work it into your project regardless of the method (css or js/css etc). <!DOCTYPE html> <html> <head> <title>CSS :target Practice</title> <style> ul.tabs { margin: 0px; padding: 4px; list-style-type: none; font-weight: bold; } .li { padding: 4px; border: solid 1px #ffffff; background: #ffffff; } #tab2content { display: none; } :target { border: solid 1px #009900; background: #e0e0e0; } #tab2:target { font-size: 24pt; } #tab2:target > #tab2content { display: block; } </style> </head> <body> <h1>CSS :target Practice</h1> <p><a href="#tab1">Short Description 1</a></p> <p><a href="#tab2">Short Description 2</a></p> <p>...</p> <ul class="tabs"> <li id="tab1">!Product Enquiry</li> <li id="tab2">Product Enquiry <ul id="tab2content"><li>Hello Product seeker</li></ul></li> </ul> </body> </html> https://www.w3.org/Style/Examples/007/target.en.html https://developer.mozilla.org/de/docs/Web/CSS/:target I hope that this is helpful, John
-
I'm not being rude but math involves numbers. <script> document.write(screen.width); </script> - 20 = not valid mathematics. you must realize that you are assigning a string to the $screenwidth variable and not a number. if you use a number then the following code will work: $screenwidth = 3072; echo $screenwidth - 20; As a string, you could echo the string where you want the script to execute within the dom. But then you cannot use the JavaScript to assign the value to a php variable. PHP is a server-side scripting language. JavaScript is a client-side scripting language. I hope that my post helps you understand what is wrong with your logic.
-

Going insane. Ajax call sets session as expected but does not persist.
jodunno replied to jtorral's topic in PHP Coding Help
Hi jtorral, I think that, based upon your posted four-point problem, responsive css is a better method than trying to use php to respond to media sizes. https://developer.mozilla.org/en-US/docs/Web/HTML/Responsive_images media queries can also help for images or overall css adjustments for "other functions on the page like resizing pop up boxes and so on" https://developer.mozilla.org/en-US/docs/Web/CSS/CSS_media_queries/Using_media_queries when you veer away from JavaScript driven pop-up dialogs and move to css modal methods, the above methods will save you alot of hassle, such as trying to post to an included php file and expecting it to receive the post. Have a look at the css and try that method instead. The session should be used to maintain state, which includes databases by storing a user id for repeated querying. You could post CSS questions in the CSS Help forum: https://forums.phpfreaks.com/forum/17-css-help/ And have a second look at what Gizmola posted, John -
easy to forget, i guess. I'm used to working on my own projects on an up-to-date xampp installation. I just forgot that we have an outdated dump file. I suppose that it is simply a common mistake when focusing on the code. I have found several resources on the recursive cte topic: https://dev.mysql.com/doc/refman/8.4/en/with.html https://www.mysqltutorial.org/mysql-basics/mysql-recursive-cte/ https://bobcares.com/blog/mysql-recursive-cte/ https://mariadb.com/kb/en/with/ https://mariadb.com/kb/en/recursive-common-table-expressions-overview/ https://matthewdaly.co.uk/blog/2022/12/18/two-techniques-for-handling-recursive-relationships-in-mysql/ I'm going to play with this concept to gain some experience as quickly as possible, although mastering the subject will cost some time. Very fascinating. I need to upgrade my knowledge of sql in the process of this forum. Thanks for the tip, Barry. Now please spend some time relaxing. I have to log off now as my son has an appointment with a doctor. I will be back in a few hours, then i will continue upgrading my sql skills.
-
yes, of course. I seem to have forgotten that i am using a dump. I need my coffee. LOL but it works with INTERVAL 2 WEEK. meantime, i'm reading about temporary tables, what a fascinating and useful method of retrieving data without effecting permanent storage. I'm enjoying this concept.
-
yes i see that the recursive code is working. Thank you for correcting me. At least i learned how to use aliases with JOINs. I also Thank you for educating me on this subject. hmm. the query that you designed is working but the last line of sql is returning an empty set for me. I'm using xampp with mysql mariaDB. if i replace the last line with LIMIT 20 to test that the query is working, then i get results. Something is not working with the date. Do you know why?so WHERE FROM_UNIXTIME(p.time) > CURDATE() - INTERVAL 7 DAY
-
I'm sorry that it didn't work out for you after three hours. I should've included the table structure in the file. My apologies for not properly planning. Barry, you never cease to amaze me. Your code is fantastic and you only had the structure to work with. I hope that i can get my level of sql programming to such a position as to build from table structure alone and it works. I still have trouble with advanced sql since i have neglected this language. But i am learning from you. I decided to take this JOIN concept with aliases and put it to practice. I had displayed the board index forums using basic sql but i noticed that a board structure table exists. I thought that i should be loading the forums according to the board structure, so i implemented your sql concept to arrive with the following query: select s.parentID, s.boardID, s.position, b.title, b.description, b.boardType FROM wbb1_1_board_structure s JOIN wbb1_1_board b USING (boardID); it works 🙂 i have the forums displayed in the order specified in the board structure table. More importantly, i learned from you -- pending your approval. i would like to rebuild the database because from day one i have had a difficult time looking at it. I am not a db architect and my level of sql is currently basic or entry level. However, from what i knw about db design from you and a few others at this forum, the db is not correctly designed. I also do not understand why username and userid has to exist in every table. I thought that one is supposed to relate the tables using a common field, such as id. I do not see this being implemented. But my first goal is to upgrade the php, html, css and sql to php 8, html 5 , css3 and pdo. Then i can look at the db but then i suppose that doing it this way will mean that i have to rewrite the sql parts of my current code. So i have to think about that. Once again, my dear friend, Thank You. You have helped me more than you know. I am going to keep reading sql tuorials in my free time. I need an upgrade too 🙂 Please get some rest, Barry and i hope that your Netflix binging was entertaining and satisfying.
-
Thank you. You should know that i have a text file of data that you have posted. I always appreciate the wisdom from the top talent here at phpfreaks. I have learned alot from this forum and its top members. I give credit where credit is due. I actually learned how this JOIN is working and i have successfully implemented my own query on the db last night before bed. I'll post the code in a reply to Barry. My point is that i learn from Barry and not simply take code and be on my way. I'm not looking for a free ride, only help when something is above my current level of knowledge. I hope that you have a splendid day, Gizmola.
-
Hi Gizmola, very helpful post. I've read about this topic for quite some time today and it is very fascinating to me. I should've explored sql many years ago but atleast i'm trying to catch up now. I have learned alot from Barand but i never implemented it with my own code to gain experience. I am learning alot today and your notes are also very helpful. I see how it is working now and it is quite clever 🙂 Thank you for taking time to educate me on this subject. I appreciate your expertise. I appreciate Barand's expertise always, although he may not know it. I hope that you have a pleasant evening and i'll keep experimenting with this concept to gain more experience with it.
-
I have been reading so much sql that i am getting dizzy. I need a break. I'm going to switch to the html 5 and css 3 code a bit, then i will watch a film with my wife to relax. I'm trying to convert the forum to php 8, html 5 and css 3 with better session handling and security. I hit a wall with the sql code. I just need to rebuild the posts with attachments and finish the index page, then the forum will be stabilized. I cannot believe the sloppiness of this commercial code and database implementation. Anyway, my friend is too old to battle code and i am helping him for free since i use the forum as well. Some experts are in the forum and i'd hate to see it disappear. I'm trying to rescue it from a hacking death. I can tell that sql injections are working on this forum and i believe that bots may be the reason that the site crashes with a session error. I just watched Venom Last Dance and Saturday Night movies. Very good films if you are looking for something to watch. Unless you are not a fan of Marvel or Saturday Night Live.
-
it is an alias, yes? i didn't know that we could use an alias. I only know basic sql: select what from table_name or from table_name where whatID = thisID etc. i found a cheat sheet: https://learnsql.com/blog/sql-join-cheat-sheet/joins-cheat-sheet-letter.pdf very fascinating!
-
well i have finally made a dump and sent it to you. I am still trying to find a way to instruct my brain of how i could come up with the same query that you have posted. I really need to master sql now. Not to take any more of your time but what is with the b. t. prefix. How is this working? what do i call it so that i can research it? adding b. and t. to the column seems like a reference that can be used in multiple tables. I have not seen this before...