-
Posts
4,363 -
Joined
-
Last visited
-
Days Won
11
Everything posted by Zane
-
Your wording and examples are a bit all over the place, I believe you're trying to filter an array, and then manipulate any specific ones that match particular date. Right? So, if 5/5/25 is a day with a special rate, and is within the date range provided by the user, use the "special" price? You can use array_map to manipulate the items that match a specific date. An example of it being used for only one "special" date - May 5 2025 $dates = [ '2025-05-01', '2025-05-02', '2025-05-03', '2025-05-04', '2025-05-05', ]; $specialDate = '2025-05-05'; $specialPrice = 8.00; // The special price to apply ONLY on $specialDate $priceUpdateCallback = function ($item) use ($specialDate, $specialPrice) { $element = ["date" => $item, "price" => 10]; if ($item == $specialDate) { $element['date'] = $specialDate; $element['price'] = $specialPrice } return $element; }; $result = array_map('priceUpdateCallback', $dates); echo "<pre>", print_r($result), "</pre>"; Should give you something like Array ( .............Array ( [date] => 2025-05-05 [price] => 8 ) )
-
The default port number is 3306. Is this port open? Is it even using 3306? It being your mysql server.
-
@Barand I suppose you're right https://developer.mozilla.org/en-US/docs/Web/HTML/Element/a#attributes Ironically, that page didn't scroll to Attributes section when I clicked the link. Using that site as an example, it looks like the id can be on hN elements
-
Actually, it's the name attribute to define an area of the page scroll-wise. <a name="middle-of-page"> Then you can have your link with the name in it <a href="#middle-of-page">Click to go to middle of page</a> For external usage, just put the page url. <a href="page2.html#middle-of-page">Click to go to middle of Page 2</a>
-
If you're looking for an API-esque way of doing it, you can send URL params to this place and get an image back https://documentation.image-charts.com/
-
Ah ok, this was the missing piece to my understanding. So basically each file would be given a hashed name of say 10 - 12 characters, and store that hash along with the filename given by the user in the db. And I would have a UNIQUE constraint on that column. I don't know why that didn't cross my mind, but that answers my question. Thanks Kicken!
-
So, right now, I'm working with a project that can potentially have thousands of users logging into it. At this time, it is simply in development, maybe 3 users at the moment. Regardless, the goal is to give users access to an online file editor, and in this editor, they can only see and edit their own files and folders. No one else's. The issue at hand, is I'm trying to (I want to) avoid having to create a subdirectory for every user registered. However, I'm having a hard time wrapping my head around an idea and infrastructure for organizing something like this. My first thought was to use a virtual host, but that would still entail have a directory for every single user, and having that many subfolders to maintain would be a nightmare. What if the configuration files' structure has to be changed? Then, a script would need to run to loop through each and every user's subdirectory to update that configuration file. Of course, I suppose there could be a single config file that all user's are tied to. I realize there isn't a one shoe fits all for this design, but I know this isn't the first project in the world to have this problem. I'm making every effort possible to keep scalability in mind. **These will not be Linux users or even Windows users, they will be entries in a users table in a MySQL database; just your run-of-the-mill CMS. Surely Wordpress/Github/Blogpost/etc don't create a new subfolder for every user registered? Ideally, at the surface, it would appear that each user has their own directory, but behind the scenes there would be a system in place that is only rewriting the URL to appear that way. www.website.com/user1 www.website.com/user2 and so on. When in reality, the actual URLs before being rewritten might be www.website.com?uid=123 www.website.com?uid=4833 and so on... Although I'm aware of how to setup something like that, I'm just not convinced is the most efficient solution. As it is, users will have their how row in the users table in the MySQL database, and there would most likely a be a table for files and folders with a foreign key for the user_id found in the user table. (I haven't taken into account the possibility of groups yet, that would be down the road). Anyway, I'm just curious as to what kind of solutions people may or may have not designed into their current systems that address the ability to avoid thousands of subfolders for thousands of users.. Please let me know if I need to provide more details. As I have posted this in the Application Design forum, this is mostly a theory based question. I'm not expecting a concrete copy and paste solution. I just need to warp my head around a potential solution and how I could make it work.
-
I just realized how old this thread is.
-
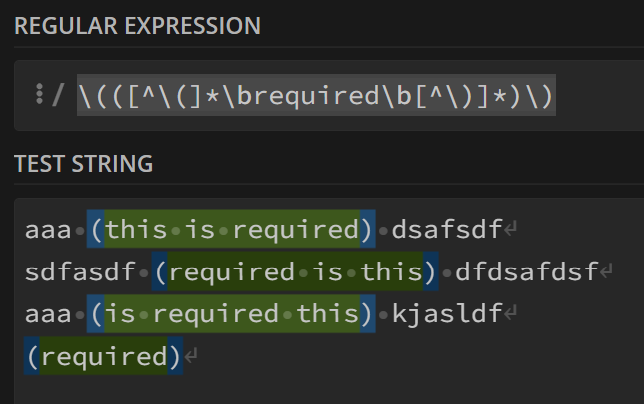
I would use the "if not" part twice \(([^\(]*\brequired\b[^\)]*)\) The \b boundaries aren't exactly necessary, but I consider good practice in case your word appears inside another word.
-

Concatenate a variable and a string into another variable
Zane replied to ziggelflex's topic in PHP Coding Help
Why do you have a period in front of $root? Besides, that, this should work (without the period) -
We're excited to announce that we have a Discord server now. We've been trying to come up with a supplemental way for users to interact, connect, learn and teach through chat. The IRC server hasn't exactly been very dependable, and we've agreed this is the next best thing. Click the link below to join us! https://discord.gg/fza5pmEjrF
- 1 reply
-
- 1
-

-
What exactly is your desired output? You provided what $final_array looks like, but you didn't clarify if that's what you're expecting. Are you simply asking for a better strategy?
-

How can I make the tryguess.php appear on the trynumber.php?
Zane replied to idk_php's topic in PHP Coding Help
In the tryguess.php file, encase the code into a function. On your trynumber.php script, include the tryguess.php script Put the HTML in this trynumber.php script change the form to POST to itself run the function, included by tryguess.php, within the HTML to output the string you want. -
Can you emphasize a bit more about your number system? As far as keeping the number, you would need to keep those in another table that has a status column called, say, "available". The value would be 0 or 1. Then, you can do a query to get or set the availability of the number. Give said table a "member" id column and you can link the two the tables (members table and the numbers) It may help if you described more what this "number" is that must be recyclable. Lastly, the rule of thumb for a normalized database is to always have a primary key that is just integer auto-incremented, nothing more. If you want to do further indexing, then add a unique index column for foreign keys to your "number" table.
-
You provided a screenshot of your desired format: a button next to a button. However, you say that it kills the page. Do you have a way of showing us that? Even if I use Developer Tools to add a button with copy/paste, it doesn't break the page and there is a button next to a button with no issue. What part of the page is killed?
-
https://www.php.net/manual/en/function.simplexml-load-file.php So using the syntax $path->name will not work and will throw such an error $simplexml_load_file returns one SimpleXMLElement But why even use xpath()? You could just do this. <?php $string = <<<XML <?xml version='1.0'?> <GoogleCodeBase> <result> <geometry> <location> <lat>LATITUDE</lat> <lng>LONGITUDE</lng> </location> </geometry> </result> <result> <geometry> <location> <lat>2nd LATITUDE</lat> <lng>2nd LONGITUDE</lng> </location> </geometry> </result> </GoogleCodeBase> XML; $xml = simplexml_load_string($string); $o = $xml->result->geometry->location->lat; echo $o; /* If you wanted the second result instead, you'd treat it like an array */ $xml = simplexml_load_string($string); $o = $xml->result[1]->geometry->location->lat; echo $o; ?>
-
Where is Line 22?
-

Manipulate PHP Array for Google Product Feed (sizes to records)
Zane replied to John_A's topic in PHP Coding Help
I completely agree with Barand. There is definitely a more efficient way of doing this, but it is your choice to keep doing it this way. You could at least set up a sandbox/staging version of your site and practice with different approaches, but that's just me saying things. In any case, we need more information: What does your table schema look like? What kind of output are your receiving? What do the arrays look like once you've looped through everything? Why aren't you just exploding on the comma? Step by step, what is going on here. Echo it all out and show it to us. We only have a snippet of your code and very vague output. I completely understand the concept of the format Google Product Feeds is looking for. You want the id of the product to be the ID in the database concatenated with a "-" and the size number. You also want to maintain that id before concatenating and use it for your item_group_id. Rather than just slapping a snippet of code on here, please walk us through the whole process. Without any substance, there isn't really a question, is there? GIGO is what they call it. Your answers will only ever be as good as the question you start with. Here's a snippet of code I like to use for debugging, which would definitely help you out in improving your question. echo "<pre>", print_r($data, false), "</pre>"; $data can be anything, a string, an array, an object, a boolean, it doesn't matter. print_r's first argument is expected to be mixed.- 11 replies
-
I would make students[modules] an array of module objects instead of an associative array with numbers in quotes. var data = { "students": [ { "name": "Eric Smith", "modules": [ { "id": "COMP40003", "name": "Software Development", "result": 80 }, { "id": "COMP40001", "name": "Digital technologies", "result": 71 }, { "id": "COMP40004", "name": "Web Development", "result": 47 }, { "id": "COMP40002", "name": "Networking Concepts and Cyber Security", "result": 0 } ] }, { "name": "Student Two", "modules": [ { "name": "Module 1", "result": 44 }, { "name": "Module 2", "result": 5 }, { "name": "Module 3", "result": 34 } ] } ] }; And then loop through it using the native array function forEach() data.students.forEach(function(i){ console.log(i.name); console.log("======================"); i.modules.forEach(function(j){ console.log(j.name + " " + j.result); }); console.log("======================"); });
-

adding multiple rows into databse incrementing one field.
Zane replied to nook6's topic in PHP Coding Help
Perhaps you should re-phrase your question because, obviously, the solutions given to you aren't what you're looking for, as you've pointed out. If you're simply trying to increment the ticket id/number by one every time a ticket is added to the table, then the above solutions are what you need. From the code you provided, it almost looks as if you're trying to place the current count of tickets purchased at the time of the new ticket insertion. For instance, George buy 5 tickets and at that point in time there had already been 80 tickets sold, so you put 80 + 5 to put in that column. Or, are you just trying to store information in a table all by itself which contains nothing but calculated values that you could have created within the query, but you want to create those values manually? Please, rephrase your question and don't just dismiss legit solutions because you don't think they'll work. Explain why they won't work before you just shrug off the efforts of the volunteering experts here. -
PHP has a handy function for this called: is_dir()
-

Implications of entity one-to-one relationships
Zane replied to NotionCommotion's topic in PHP Coding Help
OK, so that should involve: A users table, of course, that contains the height and age An attributes table, with a column for the name of the attribute and unit of measure (UOM i.e years). A user_attributes table with a column for user id, and attribute id, attribute's UOM value